Overview
RabbitMQ is a popular open source message broker, used worldwide by companies like T-Mobile and SolarWinds. Its flexibility and speed makes it easy to integrate with other applications, such as SolarWinds Orion Platform. Since we previously reported CVE-2021-29221 against the popular programming language Erlang, we suspected RabbitMQ would be vulnerable to a similar local privilege escalation attack.
RabbitMQ installs itself as a service with the Erlang service executable, erlsrv.exe. This service, by default, runs as LocalSystem and is thus an interesting target for privilege escalation attacks in Windows installations. While this particular vulnerability is not a more conventional DLL hijacking attack, it follows the same principle of insecure file permissions at the drive root. More specifically, improper configuration of permissions in the installation directory potentially allows an attacker to load arbitrary .ez files that could contain arbitrary compiled Erlang code.
For more information on service permissions, DLL sideloading/hijacking, and related issues see our previous post on the topic.
Exploitation
To demonstrate this flaw, we followed the installation instructions in: https://www.rabbitmq.com/install-windows.html. At the time of our tests, the latest version of RabbitMQ was 3.8.13, which can be found at https://github.com/rabbitmq/rabbitmq-server/releases/tag/v3.8.13.
We followed the standard installation steps, except for the installation directory, which we changed to C:\tools. This directory can be created through the installer GUI as shown:
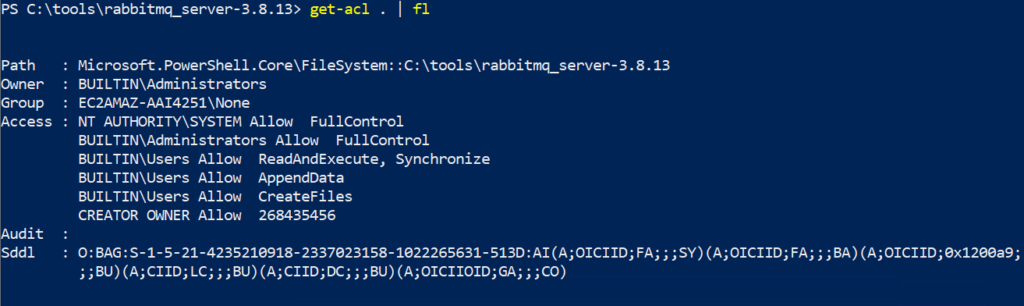
In the screenshot below, note the improper permissions, BUILTIN\Users Allow *, on the installation sub-directory, which are inherited from the drive root after installation is completed. This gives any local user the ability to create arbitrary files in the installation directory.
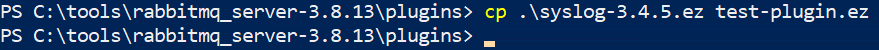
To fully demonstrate the implications of this vulnerability, first create a new unprivileged user. Then, as this user, copy one of the existing .ez files into a new file. Note how the unprivileged user has the ability to create arbitrary files.
Then, startup Process Monitor and filter by the Path by test-plugin.ez. Note how the erl.exe process which is used by RabbitMQ opens and reads from the attacker-controlled test-plugin.ez file.
As a caveat, we did not validate that the plugin is actually executed. However, we believe the fact that the plugin file is being opened and read is sufficient evidence to suggest that this is likely, since software component loading from installation paths is a common pattern with .dll files, .so files, and other software platforms. Upon reporting this issue, the RabbitMQ security team agreed with our assessment.
Because of these permissions, a local attacker would be able to gain access rights equivalent to those of the RabbitMQ process, which runs as LocalSystem.
The RabbitMQ security team was helpful in confirming our assumptions and have published a fix for this vulnerability.
The Fix
The recommended solution is to download the latest version of RabbitMQ from https://www.rabbitmq.com/install-windows.html, or at least version 3.8.16.
If this is not possible, you can also fix the permissions on the existing installation directory, for example, with the script at the bottom of our previous blog post.
Vendor Notification
| February 2nd, 2021 | Reported to security@rabbitmq.com |
| March 11th, 2021 | RabbitMQ team response |
| April 3rd, 2021 | Continued correspondence with RabbitMQ team |
| May 3rd, 2021 | Patch released in version 3.8.15. Note that this release had breaking issues for some users so the recommended version to upgrade to is 3.8.16 or later. |
| May 11th, 2021 | CVE-2021-22117 released |
Acknowledgements
We would like to thank the RabbitMQ security team for their excellent response and thoroughness in investigating this issue.
