TL;DR
Firefox is vulnerable to local privilege escalation (LPE) attacks under certain conditions on Windows platforms. This would allow an attacker to perform a local privilege escalation attack against Firefox users using the same Windows system. Through our responsible disclosure program Mozilla was contacted, and full technical details were provided, but has ultimately chosen not to fix this vulnerability.
Overview
Firefox is a popular open source web browser developed by the Mozilla Foundation.
As part of our security research and product support programs, we discovered numerous products in enterprise environments were installed with insecure filesystem permissions. One of these products was Firefox, and we decided to investigate the cause.
We found that when users choose to install Firefox on Windows in a location other than the default, it typically allows for any other user on the same system to take control of the accounts of users who use Firefox. To be more specific, improper configuration of permissions in the installation directory allows an attacker to perform DLL hijacking/sideloading attacks.
For more information on this vulnerability class, see our previous blog post on the topic, as well as similar vulnerabilities we have published to date (CVE-2021-29221, CVE-2021-26556, CVE-2021-35982).
Exploitation
To demonstrate this flaw, we first download the latest version of Firefox (Windows 64-bit English) from https://www.mozilla.org/en-US/firefox/all/#product-desktop-release. At the time of initial discovery, this was version 89.0.
We use a custom installation and change the installation directory to C:\firefox, which can be created through the installer GUI.
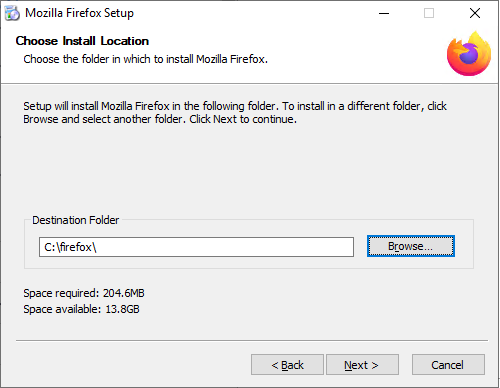
Aside from a custom installation directory, we use the default options.
In the screenshot below, note the improper permissions, BUILTIN\Users Allow *, on the installation directory, which are inherited from the drive root. This gives any local user the ability to create new files in the installation directory.
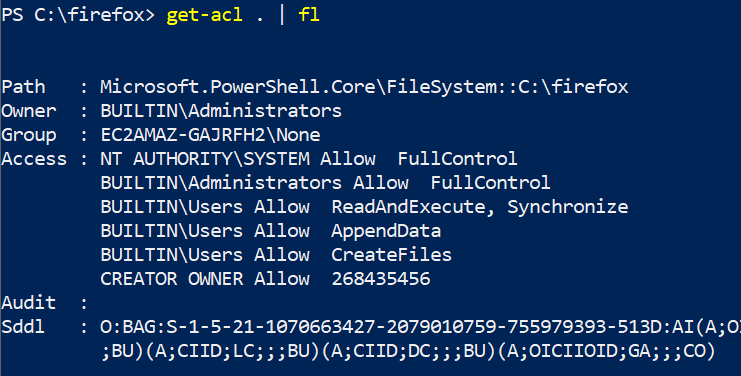
To fully demonstrate the implications of this vulnerability, first create a new unprivileged user account. Then, as this user, download the provided dbghelp.dll and move it into the C:\firefox directory. (For more information on how this file was generated, see the tooling directory.)
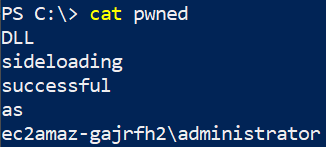
Now as the “victim” user, start Firefox. You should see a number of terminal windows appear as the payload gets executed. Assuming the default payload, you should also see a message written to the file C:\pwned.
Timeline
| June 8, 2021 | Reported to Firefox Bug Bounty. Ticket 1715334 was created. |
| June 9, 2021 | First response from Mozilla security team. Issue forwarded to installer development team. |
| July 2, 2021 | DeepSurface asked for an update. |
| July 13, 2021 | First response from installer development team, indicating they intend to mitigate the issue. Further discussion and suggestions by DeepSurface. |
| July 22, 2021 | DeepSurface asked for an update, reminding Mozilla about 90-day disclosure policy. |
| August 24, 2021 | Response from installer team. Mozilla again acknowledged the vulnerability existed, but that a decision was made to NOT address the vulnerability after all. |
| August 24, 2021 | DeepSurface requested a CVE identifier for the acknowledged vulnerability. |
| September 7, 2021 | DeepSurface repeated request for a CVE identifier. |
| September 7, 2021 | Mozilla declined the CVE request and closed the ticket. |
Recommendations
Mozilla has chosen not to correct this vulnerability. They provided the following explanation:
“Upon further discussion, we agree with the reporters that a local privilege escalation is possible here. However, this behaviour is, to our eyes, a feature and not a bug, since it enables home users to easily share an installation. That is, if you installed into a world-writeable directory (e.g., c:\Firefox), then you get a world-writeable (i.e., updatable by anybody) Firefox installation. That’s a property that we want to preserve.
Since this may not be appropriate for enterprise users, we intend to clearly document this behaviour. We intend to update SUMO and the Security Technical Implementation Guides maintained by the US Department of Defense to be clear that multi-user installations should install to c:\Program Files (required to leverage the maintenance service) or to a directory which will not inherit world-writeable permissions. Enterprise installations to network drives likely already meet that criteria.“
DeepSurface recommends all Firefox users do one or more of the following to ensure their Firefox installations are secure:
- Avoid installing Firefox in a directory other than standard paths (such as
C:\Program Files) since Mozilla does not guarantee the security of these installations. - Audit existing installations of Firefox to ensure the installation paths do not allow all users to modify the installation binaries or the folders containing them.
