With everyone working from home and IT teams struggling to scale up their infrastructure, how are you accounting for risk?
You know your organization’s employees have always been a large part of your security perimeter, but with more people working remotely, now is the time to consider how your risk has changed.
Are workers using their video conferencing tools safely? Are they more likely to fall for a spear-phishing attack now that they can’t lean over a cubicle wall to ask their co-workers, “Did you send this?” How well are their computers and networks secured?
With economic uncertainty on the horizon, what your organization really doesn’t need right now is a major breach caused by some run-of-the mill phishing attack, drive-by download, or ransomware.
How can you begin to predict where you are most vulnerable?
You do it by asking these questions:
- Which employees and contractors are most likely to fall prey to these attacks?
- For any given user, what access would an attacker gain if they were compromised?
- Are there any secondary vulnerabilities an attacker is likely to exploit once gaining a foothold in your new, highly-distributed infrastructure?
- How would exploitation of these vulnerabilities expose our “crown jewels”?
There’s a lot to think about, and the devil is in the details with this kind of analysis. What you need is a holistic view. And to get that, you need a product that can recalculate your risk on the fly based on millions of details.
Automating Your Holistic View with DeepSurface®
Automated analytics is about more than just collecting all of your risk and vulnerability data in one place. Without automated intelligence to make sense of the information, your staff are left to swim through a mountain of data. Likewise, without a way to effectively communicate the results of analysis to the rest of the organization, it’s impossible to get buy-in for security programs.
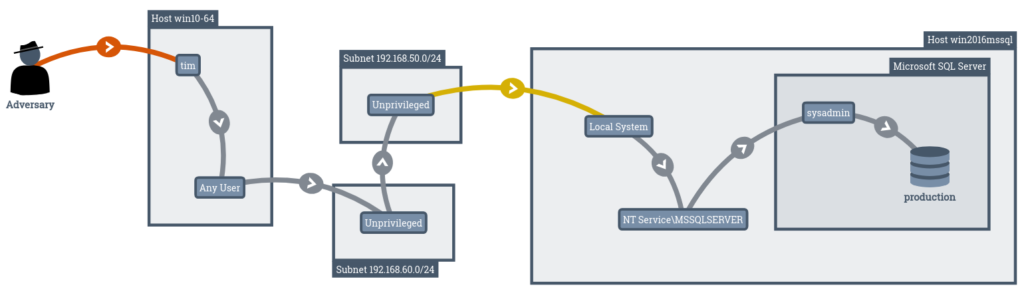
DeepSurface continuously maintains a detailed threat model of your environment, identifying which attacks and vulnerabilities matter to your most critical assets no matter how your network is changing day-by-day.
By relating the risk of attack to the level of access users have, you get a much clearer view and are provided with a clear plan of action on how to best prioritize mitigation efforts.
Key Features
- Estimates which users are most likely to fall for phishing or other client-side attacks
- Analyzes all layers of your stack, including domain access, network connectivity, and database access rights
- Connects the dots between multiple types of risks to identify the most likely attack scenarios and how they can be easily blocked
- Adapt the threat model to your situation and augment it with the results of manual security tests
- Share compelling visualizations with stakeholders to help develop consensus
DeepSurface® is easy to install and configure. Our customer success staff are ready to set it up for you. Schedule a demo today.

